Introduction
Are you looking to improve the security and assurance of your supply chain? Are you trying to meet SLSA 3/4? If so then you might be interested in improving your process for validating commits to your git repository.
This blog post will give you a high-level overview of gitsign, the latest tool from the sigstore project that provides a quick and easy way to sign your commits using ephemeral keys and transparency logging via Rekor.
Getting Started
Installing
You can easily install this on macOS with Homebrew or via the go cli.
Homebrew:
|
|
Go:
|
|
Configuring
The great thing about gitsign is that it integrates into the standard git config flows and so it can be setup both globally or for a single repo. Please see the following example on how to configure it globally (my preferred method). If you want to set it for a single repo (or disable it for a repo) you can use the --local flag instead of --global.
|
|
Usage
If you have not set automatic signing on commit using the commit.gpgsign true config you will have to use git commit -S to explicitly tell it to sign your commits. Otherwise the process is simple! Just commit as normal and you will notice that a web browser has opened.
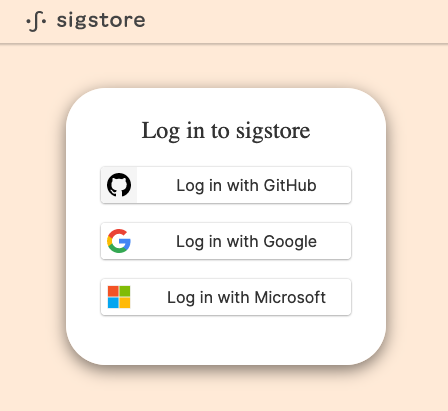
Once you authenticate, the commit will be submitted and can be verified using git log --show-signature. Unfortunately, GitHub and the other forges do not recognize this signature and it is displayed as unverified but we are hoping 🤞 that will change sometime soon.
